Multi-Factor Authentication
In today's digital age, protecting sensitive information is more important than ever. Traditional username and password authentication methods are no longer enough to keep cyber threats at bay. This blog explores how Multi-Factor Authentication (MFA) provides a robust solution through its layered security approach, requiring users to verify their identity with two or more factors. Learn about the key types of MFA methods—including knowledge-based, possession-based, and biometrics—along with advanced options like location-based and adaptive authentication. Discover the critical role MFA plays in thwarting cyberattacks, securing cloud environments like Office 365, and safeguarding digital identities in an increasingly connected world. From basic OTPs to cutting-edge AI integration, MFA is a must-have security tool for modern organizations and individuals alike.
Gage Olson
12/5/20244 min read
Enhancing Security with Multi-Factor Authentication (MFA)
In an increasingly digitized world, where a majority of our personal and professional affairs reside online, security is more critical than ever. Yet, traditional authentication methods, such as usernames and passwords, are no longer sufficient to protect sensitive information from sophisticated cyber threats. Multi-Factor Authentication (MFA) is an advanced solution designed to fill this gap, offering a layered defense to ensure only authorized individuals can access digital resources.
What Is Multi-Factor Authentication (MFA)?
MFA is a secure authentication method that requires users to verify their identity through two or more forms of evidence, known as factors, during the login process. This layered approach goes beyond the traditional reliance on passwords by incorporating independent verification mechanisms. Whether it's accessing an online account, a Virtual Private Network (VPN), or cloud-based services, MFA plays a pivotal role in minimizing the risk of unauthorized access. As a cornerstone of Identity and Access Management (IAM) policies, MFA significantly mitigates potential cyberattacks, such as data breaches and account takeovers.
Why Is MFA Important?
The inadequacy of relying on usernames and passwords has been well-documented. Cybercriminals leverage sophisticated tactics like phishing, brute force, and credential stuffing to infiltrate accounts. These methods often exploit weak or reused passwords, exposing both individuals and organizations to significant risks.
MFA addresses this vulnerability by introducing additional verification steps, such as biometric scans or hardware tokens. The complexities of these methods make it increasingly difficult for attackers to compromise accounts, even if they have access to password credentials. As a result, MFA has become a critical safeguard against cybercrime, providing a security framework that defends personal and organizational assets.
How Does MFA Work?
The functionality of MFA lies in its requirement for users to satisfy multiple independent verification steps. One of the most common examples is the use of One-Time Passwords (OTPs).
OTPs are temporary, single-use codes generated using a unique algorithm. These codes can be delivered to the user via SMS, email, or app notifications and are often valid for just a few minutes. The underlying technology ensures that each OTP is unique, tied to the specific user and transaction, making it a secure and dynamic verification tool.
The Three Main Types of MFA Authentication Methods
To enhance security, MFA follows a combination of three primary authentication factors:
1. Knowledge (Things you know):
This category involves information private to the user, such as passwords, PINs, or answers to security questions.
2. Possession (Things you have):
This includes physical objects or digital tools that the user owns, such as smartphones (to receive OTPs), hardware tokens, smart cards, or authentication apps.
3. Inherence (Things you are):
Biometric credentials like facial recognition, fingerprint scans, voice verification, or retina scans fall into this category. These are unique physical attributes that are difficult to replicate.
A typical MFA setup combines at least two of these factors. For example, a user might need to provide a password (knowledge factor) and approve a notification sent to their smartphone (possession factor).
Advanced MFA Options
As cyberthreats evolve, so too do the features of MFA. Organizations now rely on cutting-edge technologies, like Machine Learning (ML) and Artificial Intelligence (AI), to strengthen authentication methods further. Two notable advancements include:
1. Location-Based Authentication:
This method analyzes the geographic location of a login attempt. By comparing IP addresses or GPS data, systems can block logins from unauthorized or suspicious regions.
2. Adaptive (Risk-Based) Authentication:
Rather than enforce rigid authentication policies, adaptive MFA dynamically adjusts based on contextual clues. For example, it evaluates whether the user’s behavior aligns with their usual patterns—such as logging in from a recognized device during normal work hours. If anomalies are detected, such as an unexpected attempt late at night from an unknown location, the system prompts additional verification steps.
These advanced options add granularity to access policies, offering both convenience and heightened security.
MFA vs. Two-Factor Authentication (2FA)
MFA and Two-Factor Authentication (2FA) are closely related but differ in scope. 2FA requires exactly two authentication factors, such as a password and an OTP sent via SMS. MFA, however, allows for two or more factors, providing greater flexibility and enabling organizations to layer multiple security methodologies. In essence, all 2FA implementations are a type of MFA, but not all MFA setups are limited to two factors.
The Role of MFA in Cloud Computing
With the rise of cloud-based services, MFA has become indispensable. Cloud systems have removed traditional workplace perimeters, enabling access from virtually anywhere. While this flexibility improves productivity, it also introduces significant security risks. MFA mitigates these risks by enforcing rigorous identity verification steps, ensuring that only legitimate users can access sensitive data.
Cloud services such as Microsoft Office 365 utilize built-in MFA options, including SMS codes, voice calls, and app integrations. However, for organizations requiring more advanced or customizable security features, third-party Identity as a Service (IDaaS) providers offer holistic solutions. These services integrate seamlessly with an organization’s existing infrastructure, enhancing user authentication for diverse platforms beyond Office 365.
Office 365 and MFA
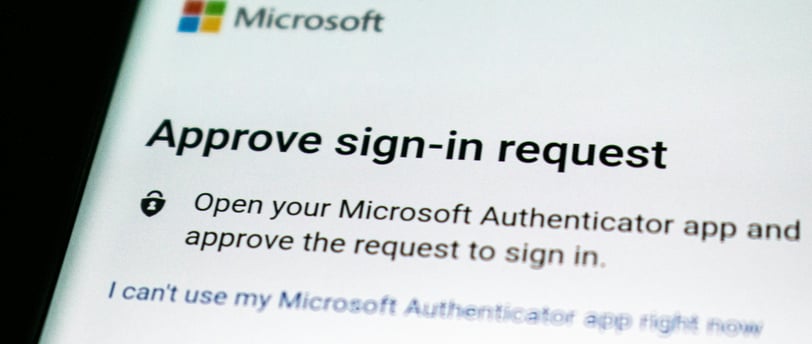
Microsoft Office 365 leverages Azure Active Directory for its MFA functionality. Common options in this framework include:
1. Microsoft Authenticator mobile app
2. SMS-based OTPs
3. Oauth tokens
4. Voice-based verification
While these features offer basic security enhancements, organizations often require premium subscriptions for access to advanced MFA settings, such as conditional access policies. For enhanced integration and wider feature sets, businesses may turn to external providers like OneLogin, which deliver robust, scalable MFA solutions.
Conclusion
Multi-Factor Authentication (MFA) has emerged as a critical security feature for safeguarding digital identities and resources. By layering independent authentication factors, MFA minimizes the risk of unauthorized access and plays a vital role in thwarting cyberattacks. Whether through traditional OTPs, advanced biometric technologies, or adaptive algorithms, MFA empowers organizations and individuals to stay ahead of ever-evolving threats.
The incorporation of MFA into modern IT practices is not merely an option but a necessity. As digital landscapes continue to expand, those relying on strong, adaptive, and scalable MFA systems will be better equipped to navigate the challenges posed by today’s cybersecurity environment.
References
https://www.onelogin.com/learn/what-is-mfa
